A few weeks ago, I got a few notifications about messages that were posted on my website, Guild Wars Legacy, which is the biggest Guild Wars 1 fansite.
Those messages were spread in various posts, all in what it seemed random locations, and all talked about an old private server (which is a tool used to run a private, local server to run the game with).
To understand this, you have to know that Guild Wars 1 never had a working private server and no real attempts to accomplish this have succeeded. So naturally, this was something that caught my attention.
After deleting those posts on Guild Wars Legacy, I went ahead and downloaded the file from the Mediafire-link that was posted. A shout out to Mediafire for deleting this file so soon after my report of the file!
So, I fired up a development virtual machine and went ahead with this malware. It was clear from the get-go that this was a suspicous piece of software, but at that point, I did not know yet how far this would take me.
On the side here, you can see how the program looks when you start it up.

Why is this suspicious?
Before we go on, a short little explanation of why this is suspicious and why you shouldn’t fall for this. First of all, like I said above, there have never been private servers for Guild Wars. If there was one, I should have known about this, but the posts in which the malware was spread said a few things that could give things away: it stated that the tools are a few years old, but when you open up the program it says (c) 2021. That doesn’t add up.
Next to that, the next few steps just give it away completely.
Please enter the path to your GW.exe… or don’t.

In the first step after clicking on the Server Setup button, you will land on this page and you will be asked to select your Gw.exe file (the main Guild Wars file). This is an attempt to make the tool look legitimate, but this step is also one where the tool/malware absolutely fails to convince me that it is.
In fact, in the file browser window that opens, you can simply click “Cancel” and it will loop through its animations and will act like it is “patching” the executable.
In reality, it doesn’t do anything at all and will display the same thing no matter what file you give it or if you don’t give it anything at all.
Even on a PC that has no Gw.exe on it at all, it will simply continue on.
In a little spoiler for later on, I can confirm that it simply does nothing, the only reason this step is here is to make you less suspicious.
The animations that play out are simply a loading bar that appears and loops to completion (always in the same time) and the lines below appear, also in the same timespan.
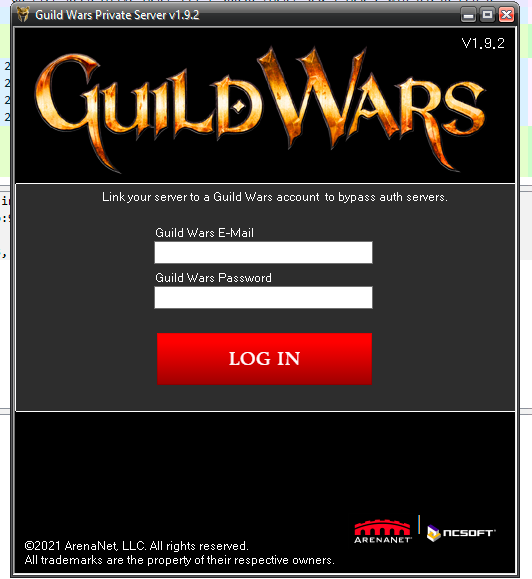
Link your account… but not really.
Now, if the previous step didn’t leave you suspicious, this step certainly should make you suspicious and leave you without a single doubt. The tool now asks you for your account e-mailaddress and a password, so that it can bypass the Guild Wars auth servers.
This makes no sense at all - if you are bypassing the auth servers, why do you need valid credentials for them? The point of a private server is that it is standalone from the main game servers and allows you to keep on playing without relying on the main server.
Whenever an untested tool that claims to be doing something, suddenly asks for your password and account e-mail should be reason enough to be suspicious. Never, in any case, enter your password here.
I entered some dummy data and some things really did seem to happen: both things that are hidden from your view as well as things in your sight. I’ll walk over what happens in the background later on.
But for now, suppose that I’ve entered something and clicked on that nice red button.
Congratulations!

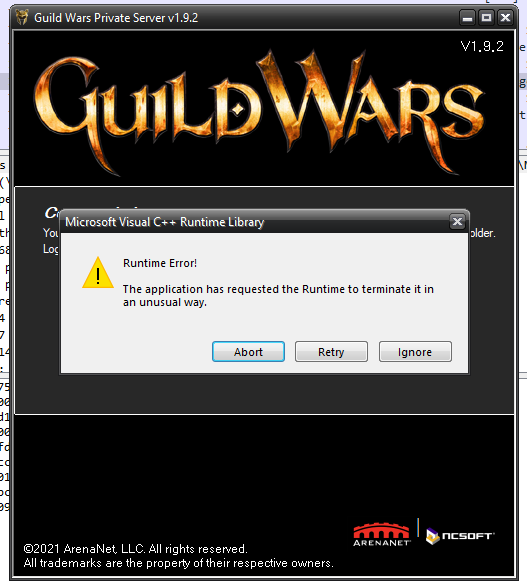
Clicking the button redirects you to this page which gives you some information and asks you to log-in to Guild Wars but to use another password.
If you click the Server Configurator, you’ll get a C++ Runtime error. How convenient, since that means that it simply didn’t work or something is amiss on your PC, right. It has to be, no?
Well, no. This is very much on purpose, and I’ll be walking through what this thing actually does in the next bit.
It’s all an illusion.
As you probably realize by now, this tool doesn’t do anything what it promises to do. But that isn’t really the surprise, we all thought about that, didn’t we?
The question ahead of us now is what it actually does, and boy, I’ll be glad to explain that.
The login-page
The first pages simply don’t do anything, they are just for show and to make it more believable. The only page that actually starts to do anything interesting, is the page that asks you to log in.
When trying to find out what the tool is doing, I went ahead and ran some tools like WireShark and Microsoft’s NetMon. These tools allow you to see what each program on your computer is trying to do with the internet. At first, the malware didn’t appear in NetMon, which means that it isn’t trying to connect to the internet. However, once you get to the login-page and you type something in the login-fields, it suddenly shows up in NetMon.
You don’t even have to type in anything, though, since it has no validation whatsoever, so you can just click on the button without input and get the same congratulations-page.
Now, once I clicked the button, this appeared in NetMon:
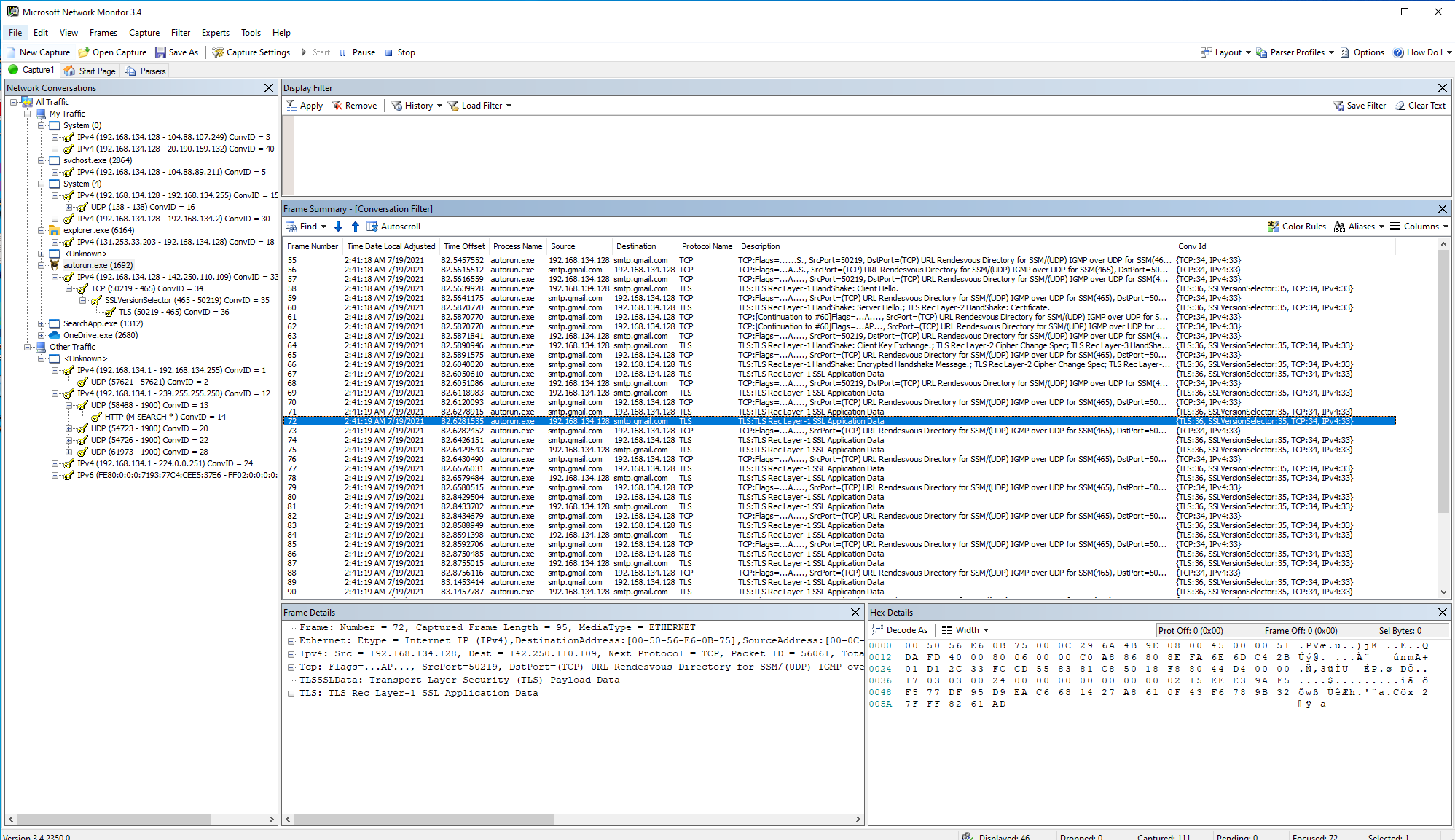
It might be hard to read here, and not everybody knows where to look here, so I’ll go over this. Once you click the button, the application shows up as autorun.exe (I’ll explain why that is later on) and contacts smtp.gmail.com. SMTP is the protocol used to send e-mails, so we can be sure that an e-mail is being sent here. The author of the malware has made a critical mistake here, though, as Gmail doens’t allow you to anonymously send e-mails - you will need to use a Gmail account and use a password to be able to send an email.
That means that both the e-mailaddress and the password are stored within the application, which means that we should be able to extract these from it. So, once I found out about this, my first step was to send out a warning on Guild Wars Legacy not to use this tool and that would actively steal your account.
The second step was to find out what the e-mailaddress was that was used here.
Finding out more about the application.
The first step here was to find out how this malware was made and how I could start to dive into it. In order to do that, I used a tool called PE Explorer which allows you to see inside an executable and get more information about how it was made and what it contains. This tool was invaluable in finding out more about the malware. Not only does it allow you to see inside the application and see what images, strings, resources are being used within it, it also gave me the literal answer about what was used to make it.
Within the version information, it revealed that it was made with Autoplay Media Studio (made by Indigo Rose) and that it was made by LG21 Patches. Autoplay Media Studio is a legitimate program that I used in the past, so I had some familiarity with it. This is used to create interactive menus for when you distribute a CD-ROM, which explains why the executable of the malware was called autorun.exe.
Due to the popularity of CD-ROMs these days, it’s become rather a niche product. It is a nice tool though to create some nice looking programs without having actual programming experience. This is one of the reasons why I expect the author wasn’t really that tech-savvy.
I suppose that the reason for using this solution mainly comes down to it having easy support for SMTP within plugins, that means that it doesn’t take that much to let you send out mails.
With that information, the next step was to extract the information from the Gw.PrSrv.exe executable.
Unpacking the Gw.PrSrv.exe
Once I had the information that I was dealing with an AMS-application, I was able to use tools built for extracting the files from AMS-projects. There are a few of those around, but the one I used was AMS Unpacker which worked as a charm and extracted all the files for me.
Browsing through the unpacked files
This then allowed me to search even further for information. One of the first things that I noticed about the malware, was that it was 92 MB big, so I wondered what was making it so big. That quickly become apparent when I noticed that a videofile of 82 MB was included in the unpacked files and a smaller second video was included as well.
The smaller file was an example video, but the big videofile was an old trailer for Guild Wars 1. At least the hacker tried to put in enough Guild Wars in there.
Going through the other files, nothing really caught the eyes, apart from the Guild Wars 2 logo in there and a few other assets. What did catch my eye, was the _extracted_cdd folder which contained some dat files.
You can’t read those with a normal text editor, but with some special tools, you can open them up and read information from within the file itself.
Casting a HEX-spell
Hex-spells are a type of spells within Guild Wars, but in this context, I’m talking about a HEX-editor. This allows you to look into binary files and extract some information directly from it.
It is here that I was able to not only extract the e-mailaddress that the mails were sent to, but also the password itself from the Gmail-account. I was able to extract quite some further information and notified both Google’s abuse teams, the local police office as well as the ArenaNet legal team about the information that I found.
I will not publicly post this information here, parts of it can already be found on the Guild Wars Legacy website, but let me assure you that this was a very stupid move on behalf of the author of the software. Let’s call him Jeff for now, because that is his real name and that’s as far as I’ll go here.
Jeff has written this program with the explicit intent of stealing credentials, these dat-files leave no doubts at all: it clearly states that it will say that the server installed, only if the e-mail was sent succesfully. It does nothing else at all, it contains nothing but lies and attempts to steal accounts.
Remember, never trust some strange downloads on the internet. And to Jeff, enjoy knowing that all information that I could find are currently in hands of the police.
If you have questions, or if you want to go more in-depth about this, feel free to contact me.
- Kevin